Introduction
Tools like Microsoft Teams, Slack, and Google Meet have become vital for businesses of all sizes. These platforms enable seamless collaboration, quick communication, and efficient workflows that transcend traditional office boundaries. However, the convenience that makes these tools indispensable exposes organisations to an alarming threat: cybercriminals masquerading as IT support.
Over the past year, cyber gangs such as Fin7 and Storm-1811 have zeroed in on productivity and collaboration suites, leveraging default settings and user trust to mount highly effective social engineering attacks. Drawing on my experience in cyber security and incident response, I want to shed light on how these impersonation tactics work—and, more importantly, what organisations can do to protect themselves.
The Rise of IT Support Impersonation Attacks
In the past, phishing emails were the most common vector for impersonation scams. Attackers would mimic internal staff or trusted service providers in emails, hoping to trick someone into clicking a malicious link or downloading a harmful attachment. However, as companies embraced real-time collaboration platforms, criminals recognised an opportunity to move beyond email and strike where employees were least suspicious.
- Integration and Collaboration: Modern businesses rely heavily on productivity tools. Organisations often embed these platforms into their customer support and sales lifecycles, making external collaboration ordinary and necessary.
- Default Configurations: Out-of-the-box settings in tools like Microsoft Teams often reveal too much information. For example, external parties can see a user’s status (online, busy, offline), out-of-office messages, or even if someone is logged in from a mobile device.
- Ease of Use Over Security: Collaboration suites aim for minimal friction. This user-friendly design can inadvertently offer attackers a simplified route to impersonate legitimate IT support staff.
Exploiting Convenience: How Criminals Bypass Defences
When you receive a new message in Microsoft Teams, the default behaviour prompts you to accept or reject it. Unfortunately, many overlook this red flag—especially if the name matches someone they already know. Criminals exploit this oversight in various ways:
- Impersonating the Internal IT Department: Attackers purchase a domain resembling the company’s real domain and create a Microsoft 365 tenant. They set up support-like email addresses or mimic known IT staff, often gleaning names from platforms like LinkedIn.
- Impersonating the Company’s MSP (Managed Service Provider): Criminals replicate that provider’s brand by researching which external provider supports a target’s IT estate—through public testimonials, news articles, or simple Google searches. They again create near-identical M365 tenants and user profiles to fool unwary employees.
- Impersonating Microsoft Support Directly: In these instances, attackers create generic Microsoft support accounts (for example, “support@microsoft365help[.]com”) that appear official at a glance, especially to busy employees looking for quick fixes.
Red Flags and Behavioural Indicators
Employees play a critical role in stopping these impersonation attacks. Here are the key red flags to watch for:
- Unexpected Contact: If you receive a first-time message in Teams from someone claiming to be IT, ask yourself whether you’ve interacted with them. If they appear to be a known colleague, but you must re-accept a “new” conversation request, that’s a strong sign something is amiss.
- Similar-Looking Email Addresses: Criminals often rely on subtle differences like “support@company-it[.]com” instead of “support@companyit[.]com.” Train staff to hover over contacts and scrutinise them.
- Unsolicited Attachments or Links: Even if the “sender” appears legitimate, verify any unexpected attachments or links through a secondary channel (e.g., a known phone number or company ticketing system).
- Lack of Official Process: Has the message bypassed your usual support ticketing system or helpdesk procedure? Any deviation from established processes warrants scepticism until the sender is verified.
Technical Safeguards and Policy Enhancements
1. Restrict External Access in Teams
Configure Microsoft Teams to block or limit external tenant communications. This step alone can drastically reduce the pool of potential malicious contacts.
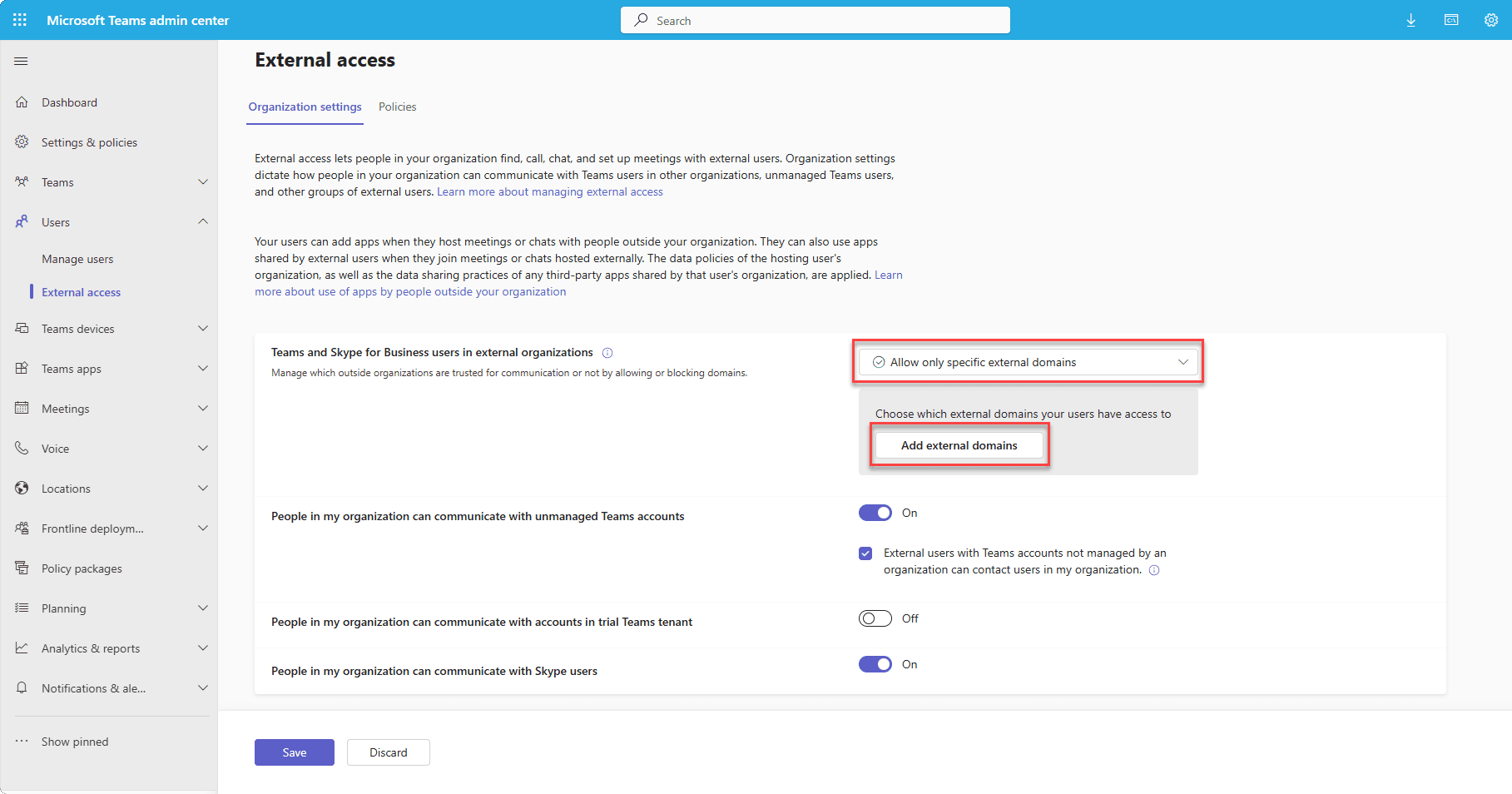
To implement yourself, navigate to the Microsoft Teams Admin Center -> Users -> External Access.
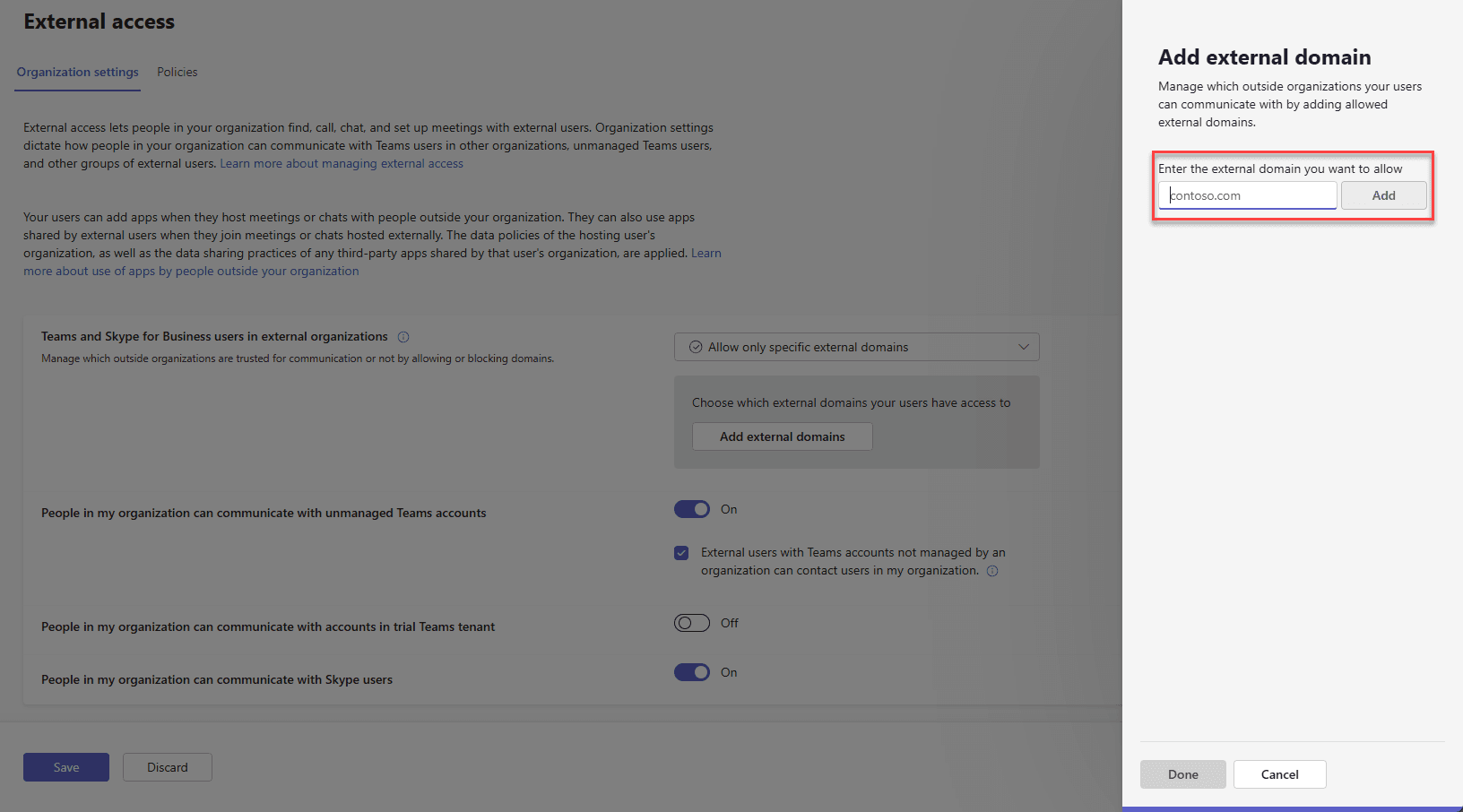
Select “Allow only specific external domains“, and add the domains for any partners or customers you work with.
Please note that it can take an hour before the changes take effect, and Teams may restart once it picks up the changes.
In addition, after setting external access, your staff can no longer send or receive messages to any external Microsoft 365 tenants who are not on the approved domain list.
To get a list of all domains your users communicate with, navigate to the Microsoft Teams Admin Center -> Analytics & Reports -> Usage Reports, and run the External domain activity report.
A process will need to be established for adding approved Microsoft 365 tenant domains during the onboarding of new customers/partners, etc.
2. Strengthen MFA and Conditional Access
Modern attacks can bypass basic multi-factor authentication (MFA) through man-in-the-middle proxies. To combat this:
- Implement phishing-resistant MFA, such as hardware tokens or certificate-based authentication.
- Configure Conditional Access Policies so only recognised, compliant devices can sign into your environment.
3. Control File Sharing and Execution
While Teams’ user interface ostensibly limits direct file sharing, attackers can still send weaponised documents or scripts via specialised tools and proxies. Deploy solutions like:
- Attack Surface Reduction (ASR) rules and AppLocker to block the execution of unauthorised files.
- Endpoint Detection & Response (EDR) solutions to detect suspicious activity in real-time.
4. Regularly Review Security Updates
Like any software, Microsoft Teams is susceptible to zero-day exploits and vulnerabilities. Stay informed about the latest patches and ensure they are deployed promptly across your organisation’s devices.
The Ransom Payment Ban in the UK: A Game-Changer
With the UK government proposing to ban ransom payments, organisations may need to rethink their cyber resilience strategies. The shift is intended to remove the financial incentive for criminals to target UK businesses. While this policy could reduce the frequency of attacks in the long run, it also puts increased pressure on organisations to prevent breaches and recover quickly if they do occur.
Pre-emptive Measures Become Essential
- Comprehensive Backups: Regular, tested backups allow you to restore critical data to a clean state before the compromise.
- Incident Response Partners: Pre-arrange relationships with cyber incident response teams that can guide you through containment, forensics, eradication, and recovery.
- BCDR Plans: A Business Continuity and Disaster Recovery (BCDR) strategy should outline immediate steps for operational continuity, including alternative communication channels like WhatsApp or Signal.
Building an Impersonation-Focused Incident Response Plan
Human error remains a persistent risk, no matter how advanced your security tools are. A robust incident response plan must address impersonation attempts specifically, including:
- Defined Escalation Paths: Train staff to know exactly whom to contact when they suspect an impersonation attempt. This might be an internal cybersecurity team or a third-party provider.
- Rapid Communication: Notify all employees when an impersonation attack is detected. Quick awareness can drastically reduce the likelihood of further successful attacks.
- Forensic Analysis: When an attempt is reported, promptly investigate. Understand how the criminal reached out, what links or files were shared, and whether any data was compromised.
- Post-Incident Review: Document lessons learned and refine policies, training, and technical controls accordingly.
A Success Story: The Value of Preparation
In one instance, a client’s employees had been thoroughly trained to verify any unexpected requests that seemed to come from IT. When a rogue account claimed to be from “Support@CompanyIT[.]com”, am employee immediately flagged it as suspicious. Because of a well-established protocol—reporting suspicious messages to a central cybersecurity point of contact—the organisation moved quickly to block the malicious tenant, inform the workforce, and prevent data compromise.
The lesson? Preparation and vigilance are the keys to thwarting these social engineering attacks.
Looking Ahead: The Evolving Threat Landscape
Attackers will adapt as more organisations tighten their default security configurations and train staff to spot impostors. We should anticipate new methods to exploit the underlying functionality of collaboration platforms like Microsoft Teams. For instance, criminals may develop sophisticated phishing proxies, code execution exploits, or advanced social engineering techniques that mimic internal organisational language and processes.
Staying ahead requires constant vigilance, regular training, and a commitment to security best practices. Organisations must balance the usability of their collaboration tools with robust safety measures that protect sensitive data and systems.
Final Thoughts
Cybercriminals impersonating IT support represent one of the most insidious threats to organisational security today. They slip into collaboration platforms under the radar by exploiting default settings, user convenience, and social engineering. Yet, these attacks can be effectively mitigated with the right combination of technical controls, robust policies, and well-trained staff.
As government policies evolve—such as the UK’s proposed ransom payment ban—businesses will face additional pressure to strengthen their cyber defences. Whether it’s restricting external tenant access in Microsoft Teams, deploying more advanced MFA, or ensuring your backups are always ready, proactive preparation is the best defence. Don’t wait for an attack before you act; build resilience to protect your data and bottom line.
If you are unsure where to start, Cyber Essentials is a great way to build initial cyber resilience into your company.
If you already have Cyber Essentials, and are concerned about any of the subjects mentioned in this article and need help with implementation or identifying further modern risks, please feel free to reach out by booking a call or check out our services below.
About the Author: David Pitre
David co-founded CSIQ, where he spearheads product development, technical innovation, integration, and automation—ensuring every engagement exceeds the highest standards.
As a Chartered Cyber Security Consultant (ChCSP) and NCSC Assured Cyber Advisor, he brings a deep passion for all things cyber, underpinned by extensive public and private experience.
Leveraging his IT engineering and cyber security background, David has successfully consulted, supported, and implemented technological solutions that empower businesses to thrive.
Beyond his professional endeavours, he relishes time with family, travelling, participating in charity walks, and savouring the great outdoors—particularly through his interest in viticulture.









