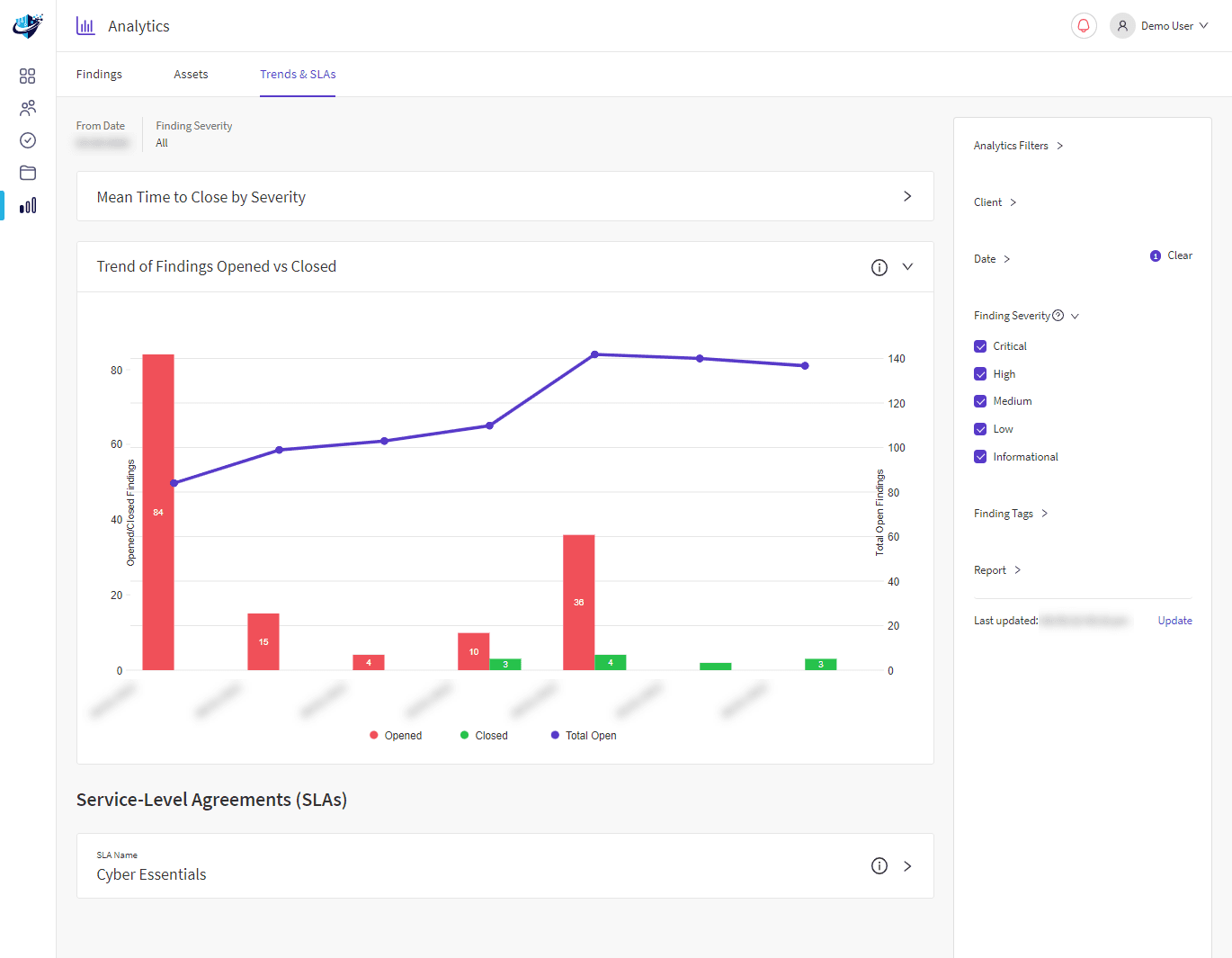
We are committed to providing Active Directory security advice that makes it difficult for an attacker to acquire access to your network. Our evaluation is designed to answer questions regarding current and future AD security project plans. We will also simulate common attacker approaches, indicating areas of concern and how to resolve them.
Additionally, we will examine your Microsoft Cloud tenant for vulnerabilities that attackers could exploit. We examine your Azure Active Directory (Azure AD), Microsoft 365, and Exchange Online environments and make recommendations to help you get the most out of the capabilities and controls available with your existing Microsoft Cloud subscriptions.
If your organisation uses Active Directory or Azure AD as its identity management tools, we can help you protect it. We will assess your configuration to reassure you that your business network is secure and optimised.