Cyber attacks are increasing, and network boundaries are becoming increasingly transparent. A managed firewall services provide many benefits for small businesses aiming to stay secure in this digital age. Implementing and maintaining these solutions can be challenging without an in-house dedicated security team, which is why we developed PerimeterIQ.
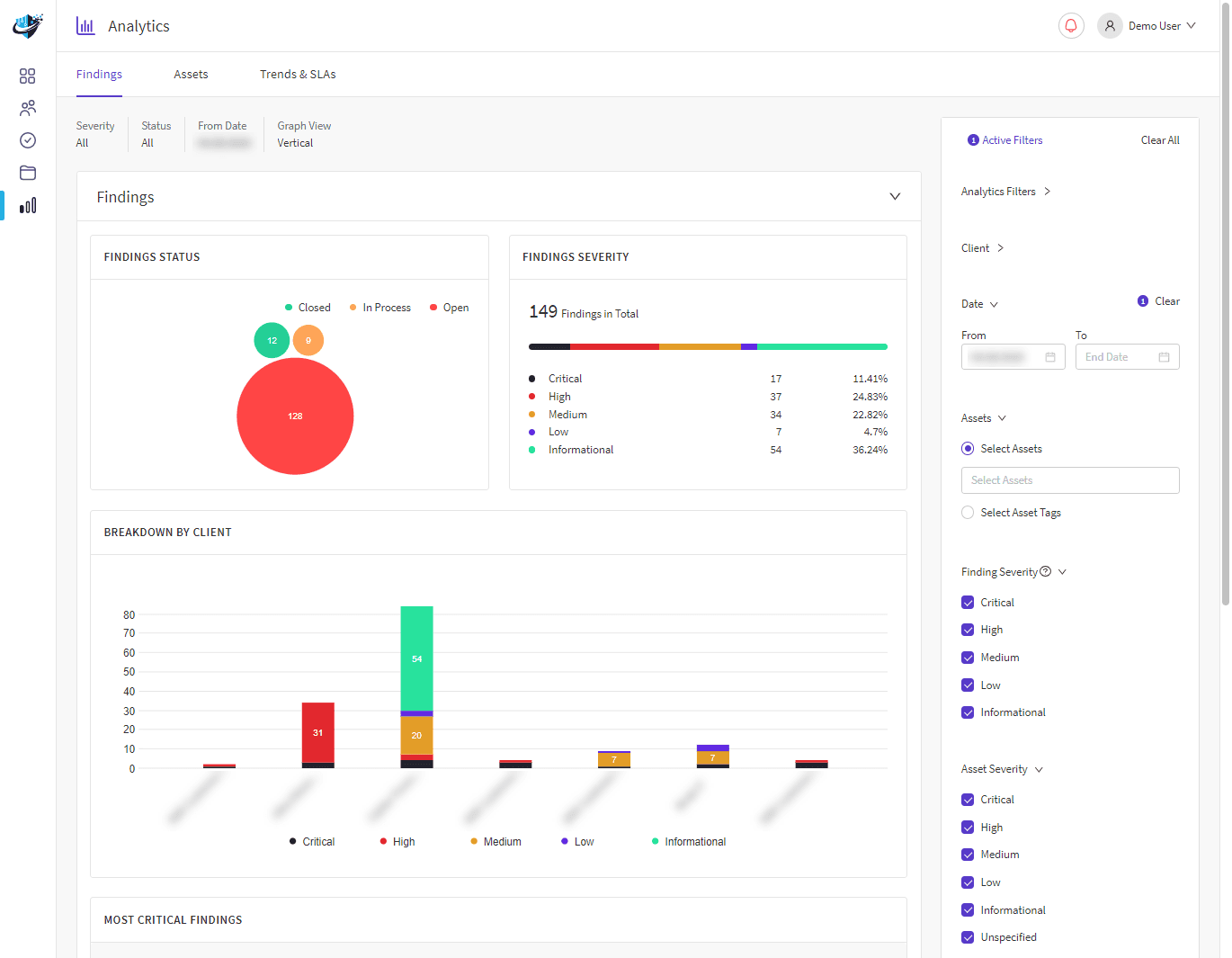
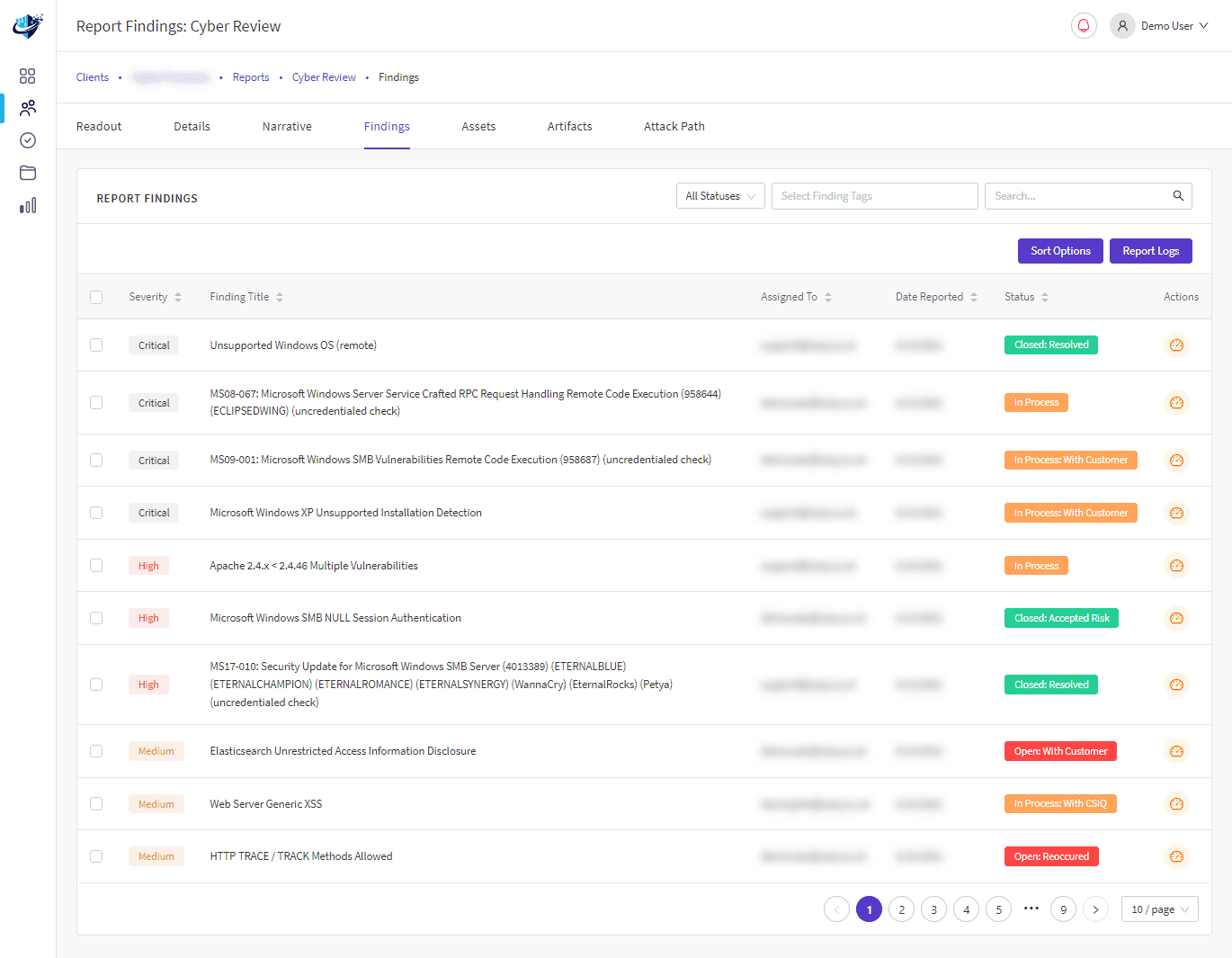
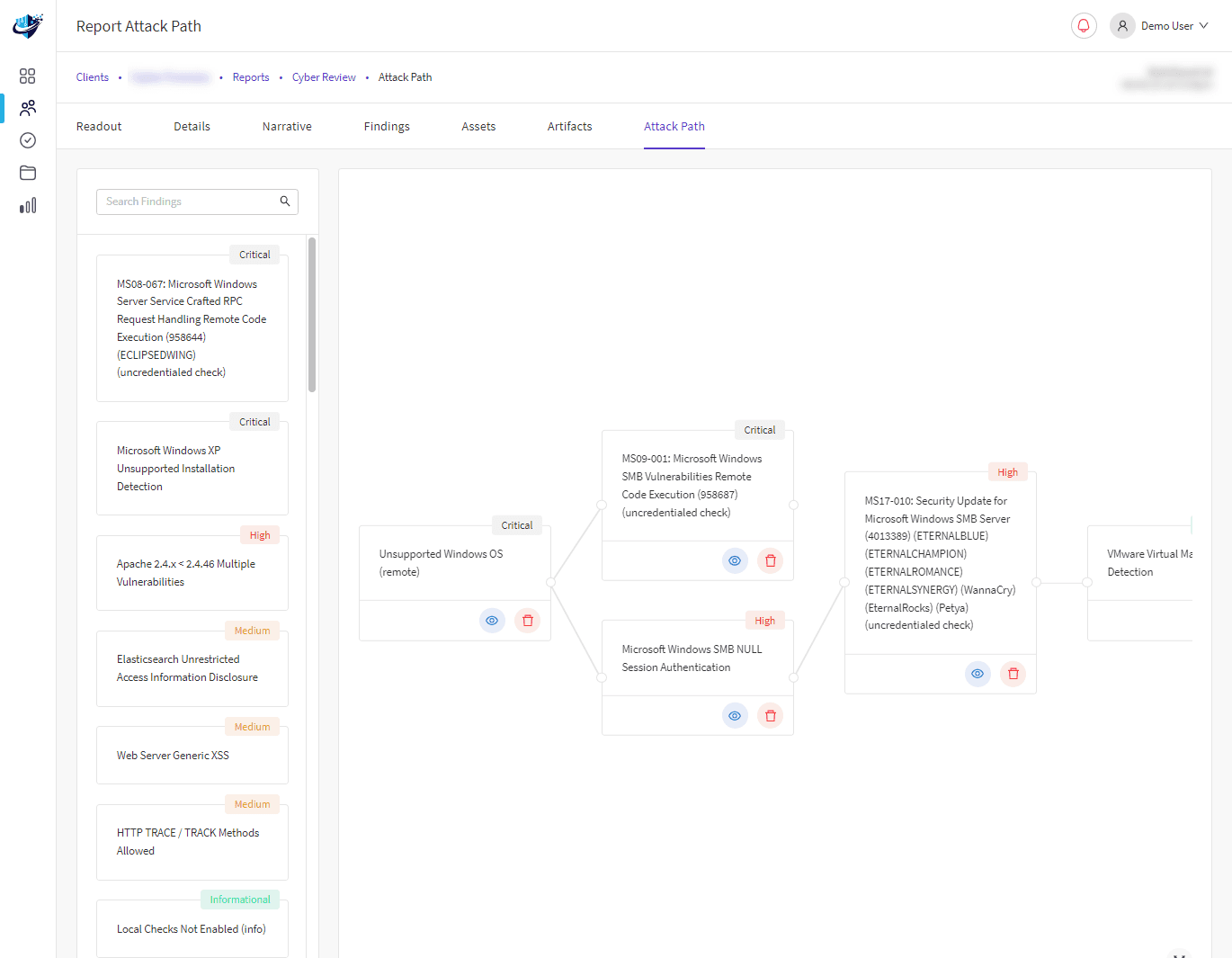
As firewall management service providers, we developed PerimeterIQ to expertly manage firewall services based on cutting-edge technology. We continuously monitor your attack surface, ensuring your perimeter remains secure and protecting you from potential attackers.